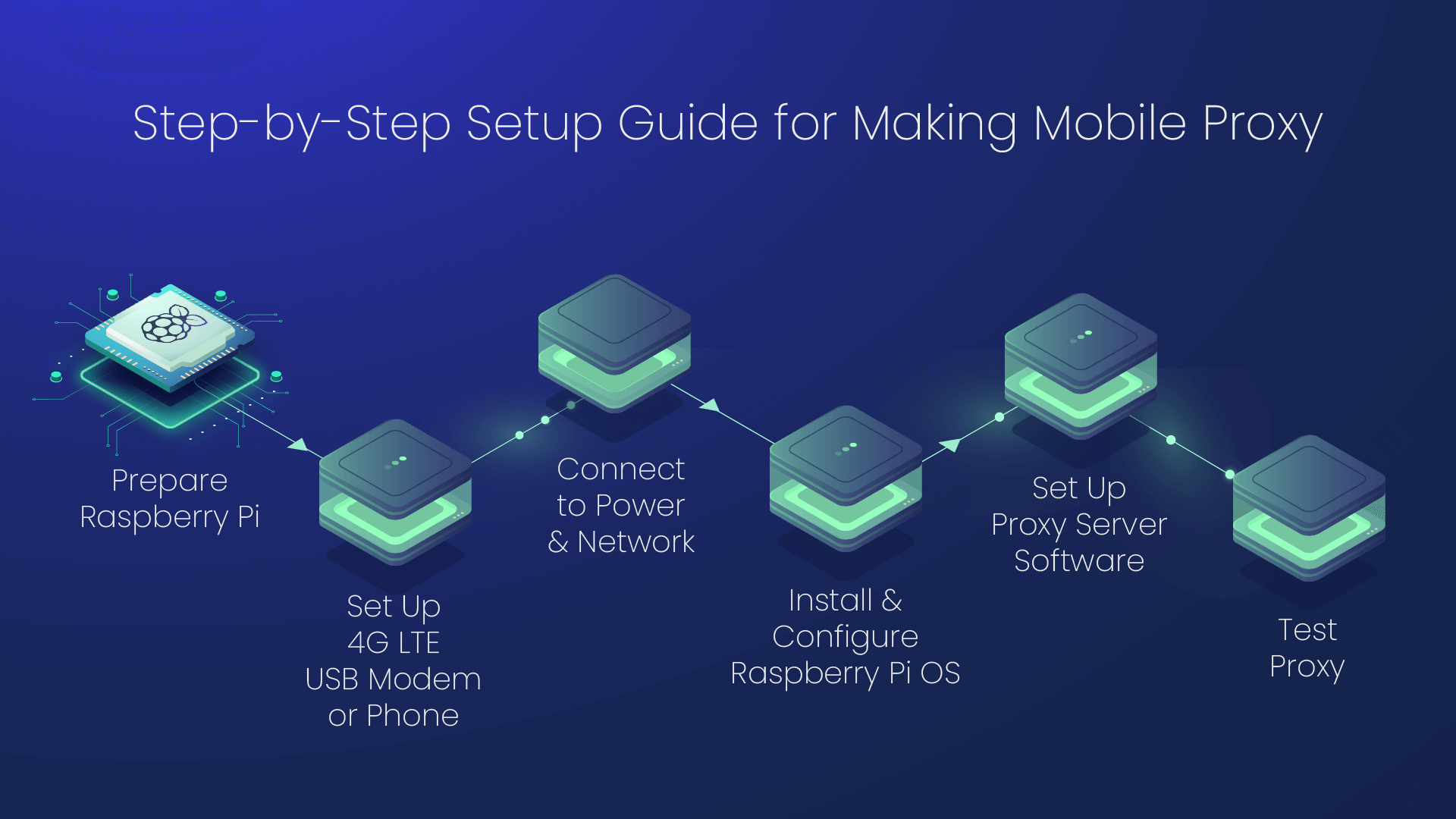
In the modern digital landscape, businesses increasingly rely on internet-based tools and services to maintain competitiveness and operational efficiency. One crucial technology that has gained prominence is datacenter proxies. These proxies serve as intermediaries between a user’s device and the internet, masking the original IP address with one from a datacenter. Their importance in business…
Tech
User Experience Review: What to Expect from SEO Tools Group Buy Platforms
If you’re looking to get top SEO tools without a high cost, consider the group buy option. They offer affordable prices and access to a broad variety of tools, as well as high-quality uptime. You can also try the service for just $1. Many users have reaped benefits by using SEO tools that are group-buy.…
Securing Your Data: Best Practices for KakaoTalk Authentication
KakaoTalk is a popular messaging application widely used across the globe. With its growing popularity, securing your data on KakaoTalk has become crucial. Authentication is one of the primary steps towards ensuring this security. By following best practices for authentication, users can protect their personal information and communications on KakaoTalk. One of the key ways…
Binary Guardian: Navigating the World of OTP Bot
These algorithms provide an additional layer of protection by encrypting sensitive data during transmission or storage processes effectively. Furthermore, OTPBot incorporates multi-factor authentication mechanisms into its framework. Alongside traditional username-password combinations or biometric identifiers like fingerprints or facial recognition scans; it adds an extra layer of security by requiring users to enter a unique OTP…
Perma-Delete Protocol: Erasing Files from the Documents Folder
Remember that cleaning up unnecessary files not only improves performance but also allows roomT-Mobile Tactics: Navigating the Login Process In today’s digital age, where almost everything is accessible online, having a seamless login process is crucial for any company. T-Mobile, one of the leading telecommunications providers in the United States, understands this importance and has…
Exploring the Differences: iPhone 15 Mini and iPhone 15 Pro
There are some things that you can be sure of in the Fall season: football season, pumpkin spice as well as new iPhones. In the past year, Apple is releasing four models, including two smaller models that are simpler to use and hold with just one hand. Which one do you purchase? These are the…
CS2 Market Strategies: Buy Low, Sell High
Studies have shown that using personalized items increases player satisfaction and motivation levels significantly compared to default options provided by games developers alone. Moreover, trading plays a significant role within this universe as well; players often engage in virtual marketplaces where they buy, sell, and trade skins with one another. This creates a sense of…
Cybersecurity 101: Understanding the Basics of Digital Protection
Develop an Incident Response Plan: Prepare for the worst-case scenario by developing a comprehensive incident response plan. This plan should outline the steps to be taken in case of a cybersecurity breach, including communication protocols, containment strategies, and recovery processes. 9. Monitor and Analyze: Implement real-time monitoring and analysis of your network traffic and system…
Transforming YouTube into Your Personal MP3 Library
With its vast collection of music videos, live performances, and user-generated content, it’s a treasure trove for music enthusiasts. However, there are times when you may want to have your favorite songs at your fingertips without the need for an internet connection or the hassle of searching for them again. This is where transforming YouTube…
A Writer’s Sanctuary: The Private Note
In this age of constant connectivity and digital distractions, finding a space of tranquility and introspection becomes increasingly crucial for writers. One such haven that writers often retreat to is the private note—a personal refuge where thoughts, ideas, and emotions find solace on paper. The private note is a timeless tool that has served writers…